The motivation for using public key authentication over simple passwords is security. Public key authentication provides cryptographic strength that even extremely long passwords can not offer. With SSH, public key authentication improves security considerably as it frees the users from remembering complicated passwords (or worse yet, writing them down).
SSH public key authentication relies on asymmetric cryptographic algorithms that generate a pair of separate keys (a key pair), one "private" and the other "public". Keep the private key secret and store it on your local computer to connect to the remote system. Conceivably, share the public key with anyone without compromising the private key; you store it on the remote system in a .ssh/authorized_keys directory.
Hands-on Exercise Overview
This hands-on exercise uses public key authentication to connect to the Ubuntu 20.04/Vagrant server by generating an SSH key pair on the local Ubuntu 22.04 machine. The connection between the local machine and the Ubuntu/Vagrant server is established using the bridged mode that allows the two machines to be in the same network.

Prerequisites:
To use SSH public key authentication:
The remote and local systems must have OpenSSH installed.
You need to be able to transfer your public key to the remote system. Therefore, you must either be able to log into the remote system with an established account username and password/passphrase, or have an administrator on the remote system add the public key to the
~/.ssh/authorized_keysfile in your account.
Steps:
Open the terminal (CTRL+ALT+T).
Verify that the ssh client is installed on the local machine:
which sshOR
ssh -VCheck for existing keys by listing the
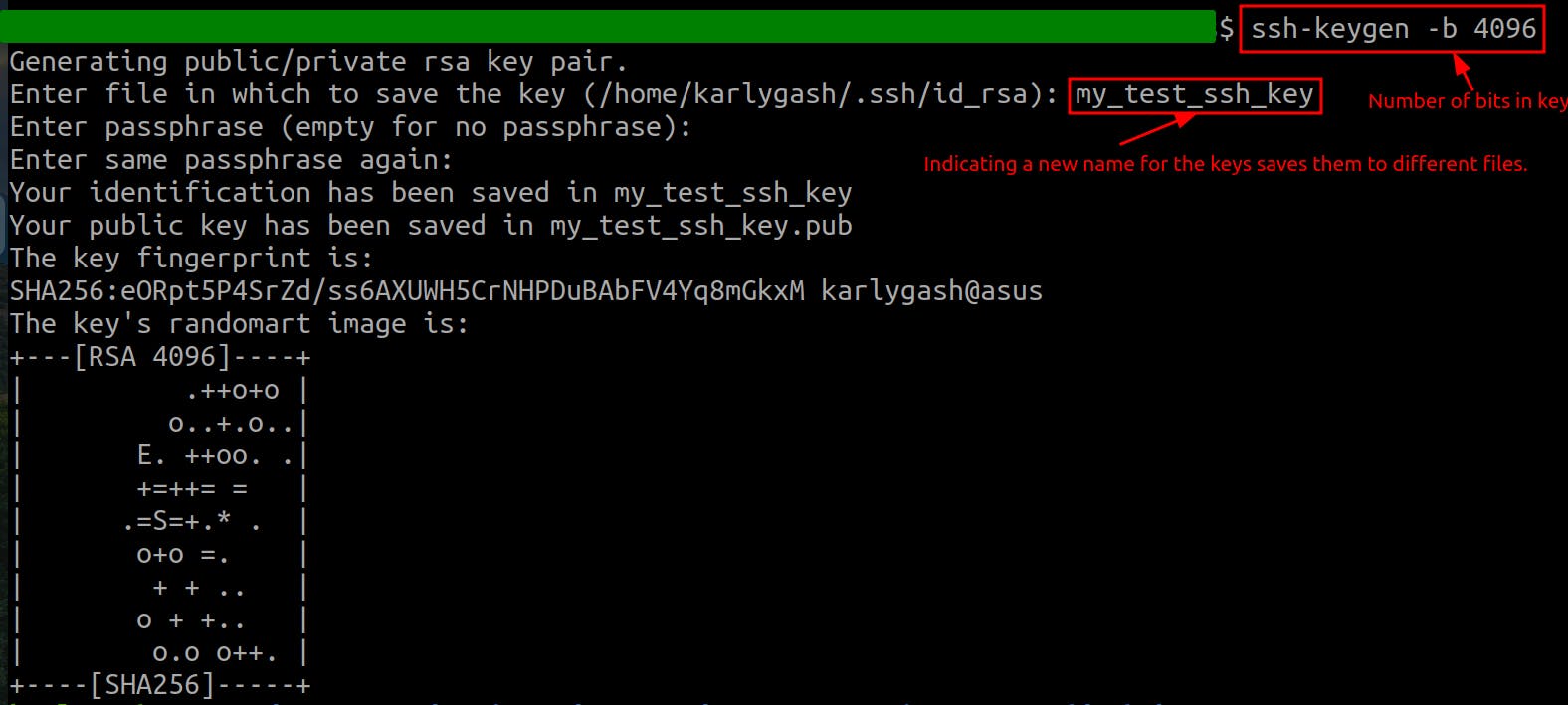
sshdirectory with on the local machine:ls -l ~/.sshGenerating new keys overwrites the current ones by default. However, indicating a new name for the keys saves them to different files.
If there are no existing keys, the output indicates the directory does not exist.
If some keys are found, they should be backed up before continuing.
Generate a key pair with
ssh-keygen:ssh-keygen -b 4096ssh-keygenis the tool used to create SSH keys, which are used for secure communication between machines.-bspecifies the number of bits in the key to create. More bits generally mean better security.4096is the number of bits in the key. This is considered a good balance between security and performance for most SSH applications.
Verify the key pair exists:

View the public key:

Check whether the server works by connecting to it first:
ssh username@ip_address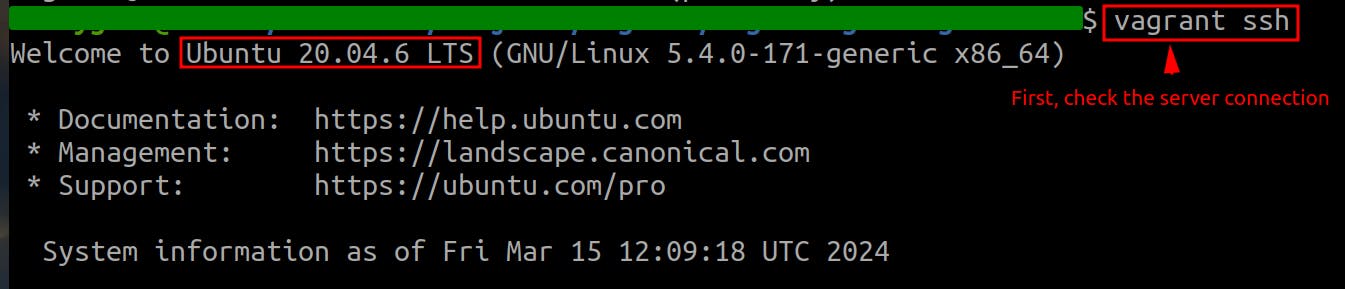
Add the public key to the server by copying it manually or using the
ssh-copy-idtool:ssh-copy-id username@ip_addressPublic keys are in the
~/.ssh/authorized_keysfile and every time a new public is added, it appears as a new one line.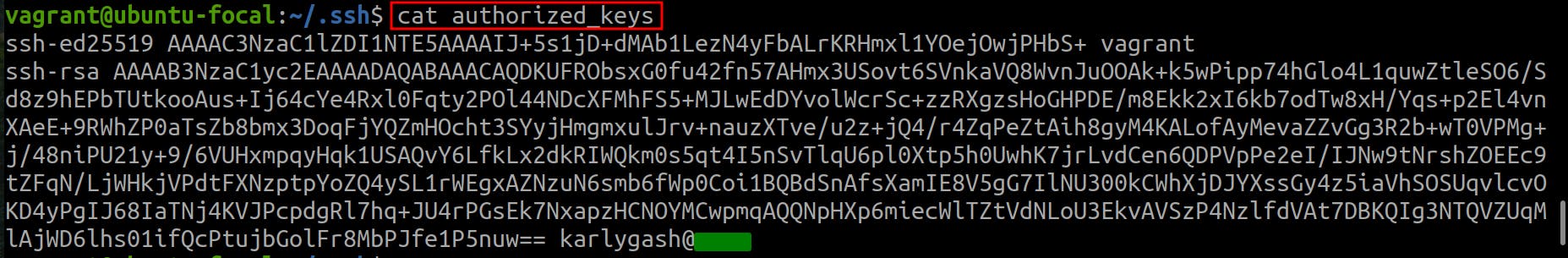
Now, connect to the server from the local machine by using the SSH private key and check whether the public key authentication works:



